
One of our recent updates is integration with Microsoft Active Directory which is helpful for using DPI in corporate networks. When organizing a corporate network, it is necessary to analyze and control how employees use Internet resources during working hours. The DPI platform is used for:
- access restriction to social networks and messengers for certain user groups
- traffic monitoring and connection analysis – to prevent confidential information leakage, DDoS attacks and BotNet detection
- fulfillment of legal requirements – restriction of access to the registry of prohibited resources.
Let’s look at how to connect MS AD and Stingray Service Gateway, create blacklists and restrict access to applications for employees.
Interaction scheme
DPI is installed in-line and ensures the passage of all incoming and outgoing traffic. The installation location is determined based on the characteristics of the network: it is recommended to install it in front of an edge router or device that implements NAT.
It is important to see the real IP addresses of clients and apply policies directly to those IPs. If you need to implement NAT, this is also possible in the BRAS and Complete versions of Stingray platform. Licensing Details
What is needed for integration with MS AD?
Stingray Service Gateway supports authorization mechanisms in the L2 (DHCP, ARP, PPPoE) and L3 (IPoE) modes, which are successfully used on broadband access networks. For example, it is proposed to use IPoE mode as the most simple and quick to configure. DPI in this scheme is very easy to scale and perform bypass using cards or a second server with a backup license.
The scheme involves:
- MicroSoft Active Directory domain controller. Authenticates the subscriber and transmits data on the issued IP address, username, group to the Radius server.
- Radius server. It accumulates information from MS AD and responds to Radius requests from DPI.
- Stingray Service Gateway. It has pre-configured profiles of black and white lists, policing profiles for blocking by protocols and applications. It generates requests to the Radius server on the first packet from the subscriber.
Profiles assignment
After authorization in MS AD, subscriber information is sent to the Radius server. When the subscriber makes the first request, the DPI platform generates an Accept-Request with the IP address of the subscriber. Based on the information that this IP belongs to a specific subscriber and group, the Radius server generates an Access-Accept with the attributes. The attributes may include:
- block-list profile name
- allow-list profile name
- name of the policing profile
- NAT pool name
- activation of subscriber statistics collection service
- activation of the notification service
- activation of the service of embedding banners for HTTP resources.
After receiving the data, Stingray Service Gateway applies restrictions for a period equal to Session-Timeout (e.g., 600 seconds). After this period, the authorization request for the IP to the Radius server is repeated.
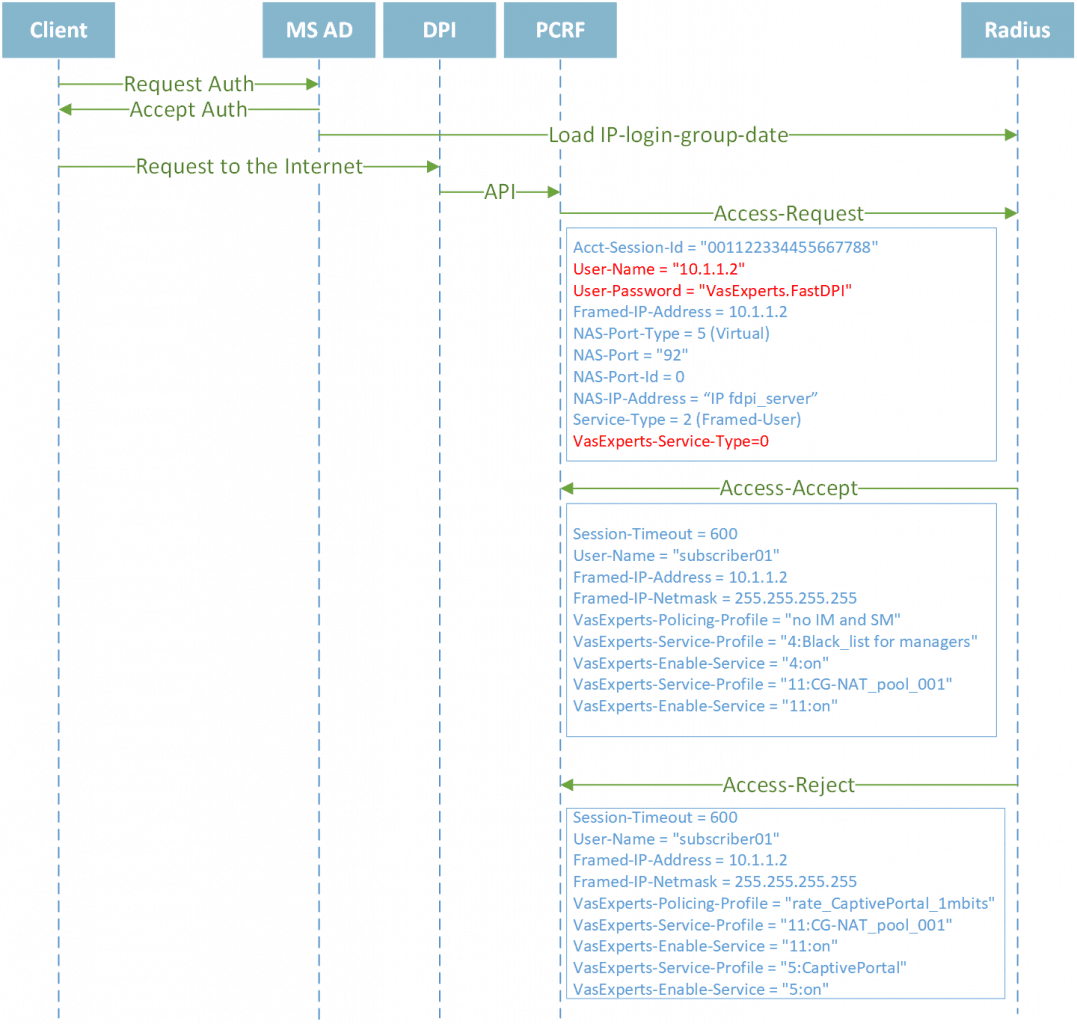
If the Radius server does not have information about the requested IP, an Access-Reject response is generated with the default profiles:
- allow-list profile name
- policing profile name.
In this case, the subscriber will be redirected to the Captive Portal at the next HTTP request and limited by the available exchange protocols.
Subscribers statistics
For easy configuration, there is a Graphical User Interface that helps to create and manage profiles, track assigned services and authorization status.
Stingray Service Gateway allows you to analyze Clickstream и Full Netflow, which is collected in the Quality of Experience module. The network administrator has the following options:
- a NetFlow statistics collector with re-export support
- API support for integration with external systems
- visualization of Full NetFlow and ClickStream statistics
- built-in reports of Full NetFlow-based TOP: high RTT, by traffic volume, by number of re-requests, by application protocols, by AS, by subscribers AS, by access switches and aggregation
- built-in ClickStream-based TOP reports: URLs, hosts, subscribers, devices, IP resources
- exporting reports using *.xlsx, .*csv, *.pdf and *.png formats
- reports on web resources categories, updating the list of categories
- full NetFlow and ClickStream reports with detailed information per user
- setting up triggers and actions on events, sending reports by email
- DDoS and BotNet detection.
