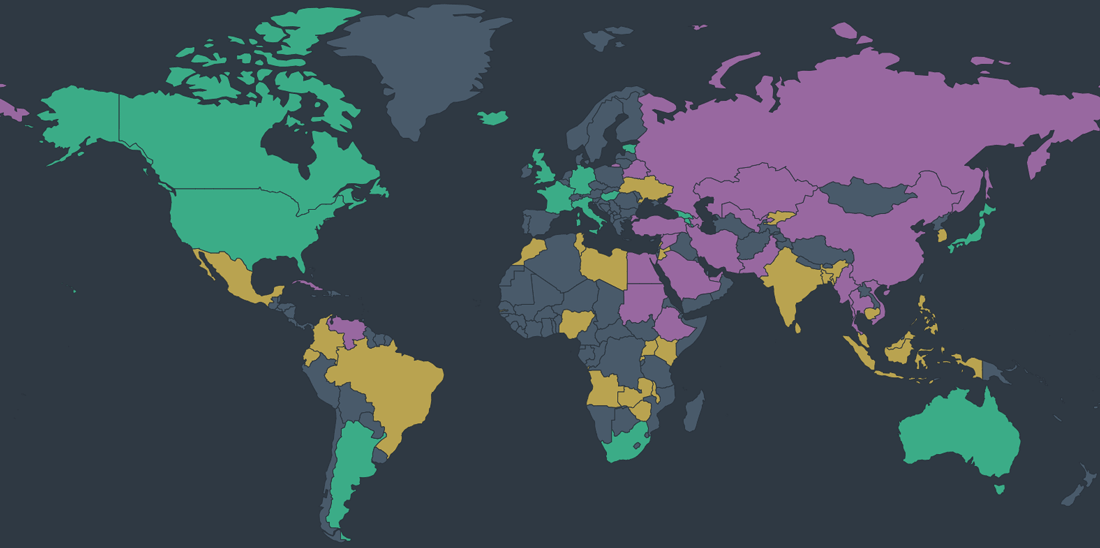
Examples of countries with government-blocked resources
Pakistan
“Freedom on the Net” report characterizes Pakistan as “Not Free” with Internet Freedom Scores 27/100 and over the years this index is steadily lowing. Due to the multiparty political system authorities frequently disrupt telecommunications to stop coverage of news and political events like it was in July 2018 during the general elections when the government shut down mobile and internet services. Over 800 000 websites are blocked due to religious and social reasons, the most restrictions refer to pornographic resources. Some research confirm the most popular websites as Facebook, Twitter, Youtube were blocked using DNS-based filtration.
Turkey
Pakistan is precisely not the only country with controlled access to web resources and social media during the political interventions. Turkey’s government instantly reacts to political events by blocking certain websites or throttling Internet traffic. In 2014-2018 the Turkish government has ordered ISPs to block 246 000 of website including Wikipedia for content that contradicts public policy perspective. Some of these blocks are temporary, such as its throttling of Facebook and Twitter, while others are sustainable. Twitter and Facebook Transparency reports state that Turkey is one of the leading countries for requests to remove content from social networks. The “Freedom on the Net” report characterizes Turkey as “Not Free” with Internet Freedom Scores 37/100.
India
In India, the situation is a bit more stable, but nevertheless, freedom of the Internet has been reduced by overwhelming shutdowns and expansion disinformation as well as misunderstanding news in social media. The government also said that in a period from 01/2016 to 11/2017, 1791 websites were blocked by ISPs on the order of the Department of Telecommunications, and 2133 websites were blocked on the order of various courts. According to information published in 2017, government blocked as many as 23,030 websites /URLs. The “Freedom on the Net” report characterizes India as “Partly Free” with Internet Freedom Scores 55/100.
In autumn 2019 there were protests in several states of India. According to The Washington Post, for more than 134 days the Internet is shut down in the Indian states of Jammu and Kashmir, which is now a record time.
How many addresses does the router process?
Governmental blocking of web resources doesn’t ease work for ISPs but there are different ways to simplify filtration and make it more efficient.
Many operators block IP addresses using BGP Blackhole or advertise only part of the BGP traffic to the filtering system. If we consider all the traffic load transferred to the router, we observe the following amount:
- The FIB (Forwarding Information Base – a table for accelerated packet forwarding) already contains about 800 000 routes;
- A certain number of routes, which depends on the size of the network, can be announced from the telecom operator;
- The governmental blacklists which differ from country to country. For comparison, “Freedom on the Net” reports divides countries into four categories of Internet Freedom: Pervasive, Substantial, Selective, Little or none. E.g.:
- Russia refers to Not Free. BGP announces about 1.5 million routes from the government blocking list.
- Pakistan – Not Free with about 800 000 routes blocked.
- Turkey – Not Free with about 246 000 routes blocked.
As a result, the router has to process from 1 million to 2.3 million addresses.
What troubles does it cause for operator hardware and why?
We are referring to hardware that is designed for processing significantly fewer routes. For example, a great number of operators have Juniper MX series routers in their network, which are able to process up to 1 million routes as set in the documentation. Back in 2009, when these models were just created, the hardware was designed for handling about 500 thousand addresses, which seemed more than enough.
Cisco SCE owners might face a similar problem soon because the processing capability of such equipment is up to 2.5 million addresses.
This kind of overload leads to route exhaustion of memory, which in turn evokes disturbance in router performance and can cause a network shutdown. Some hardware already can not cope with the load, and line cards containing up to 2.5 million FIB prefixes can exhaust their resources very soon if the number of blocked IPs continues to increase.
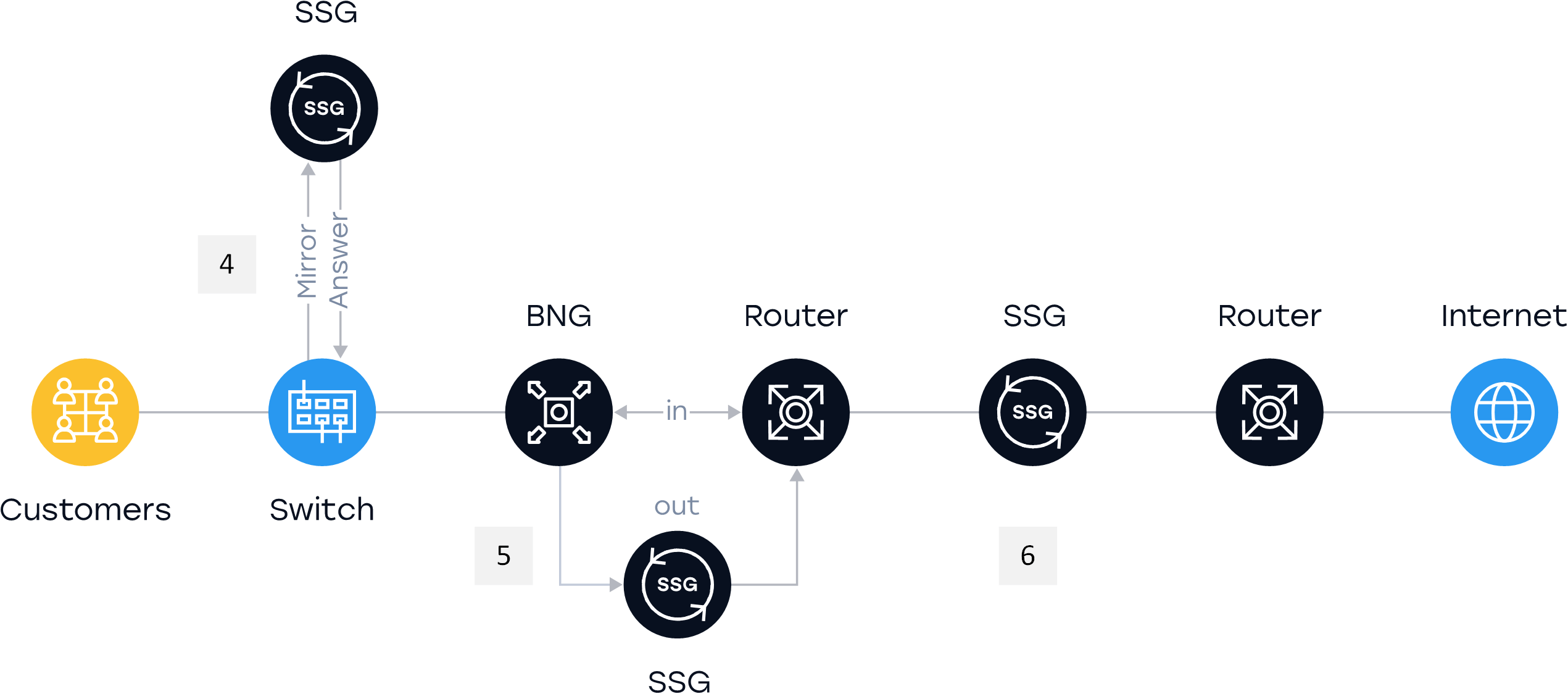
To filter a large number of routes, we use DPI blocking type with the “in-line” implementation scheme. Filtering is performed by DPI. The Stingray platform can handle up to 4 billion records.
An important aspect of DPI application is the transition from IP blocking to moderate blocking by URL, SNI, CN, and, if necessary, IP + port.
Blocking schemes
Let’s have a look at various traffic filtering schemes and mark the pros and cons of each appliance.
- BGP Blackhole: the router drops packets in the direction of a given IP address or subnet.
Pros: Implementation on any equipment.
Cons: It demands to prepare a list of resources for the router. The complete blocking may trigger negative feedback from subscribers. It also creates additional load on the router. - DPI implementation on pre-filtered outgoing traffic: traffic is selected by BGP or PBR on certain ports (80, 443).
Pros: Reducing the cost of implementation and decreasing usage of processed traffic.
Cons: Additional load on the router and possible omissions on prohibited resources, as not all traffic is filtered. - DNS based filtration: The DNS server includes a list of prohibited content and focuses on examining and controlling DNS queries.
Pros: fast implementation and the low cost of usage.
Cons: Сhanging domain names takes place in user end side. It makes it easier to evade the DNS solution.![traffic filtering schemes]()
- DPI in the “mirror” operation mode: processing through optical splitters or active equipment using SPAN ports.
Pros: no impact on the network in the case of a network fault.
Cons: This method occurs possible access to prohibited content and excludes a scenario of blocking IP or subnet due to impossibility to limit the initial request from the network. - “Inline” implementation scheme only for outgoing traffic: the requested access from the end-user to the Internet is provided via blocking device; incoming traffic is handled without any processing.
Pros: lower cost of this solution as the usage of outgoing traffic is significantly less.
Cons: this solution focuses on dividing network flows, which makes the network more complex and demands additional ports. - “Inline” implementation scheme for incoming and outgoing traffic: implemented by passing all traffic through the filter.
Pros: The ability to use all capabilities of DPI to increase QoS / QoE, the implementation of the statistics collection / BRAS / NAT functions.
Cons: Increased implementation costs compared to previous approaches, more points requiring redundancy.![traffic filtering schemes]()
Thus, it is possible to solve the problem of congestion and malfunctions of routers by changing the filtering method. it is necessary to remove the load from the device caused by the announcement of additional routes and configure the “In-line” or “Asymmetric” implementation scheme.
Contact us to learn more about Stingray Service Gateway functionality and capabilities.