Lawful Interception
Service description
Access mechanisms differ from country to country, and even within regions. But the basic principles are: the interception target affects a specific user only; the subject of interception should not be aware of the procedure.
Lawful Interception plays a crucial role in assisting law enforcement in countering organized crime. Each country carries it out in accordance with national laws and local legal requirements and practices. For example, European Union certifies LI via ETSI (European Telecommunications Standards Institute). The U.S. regulates LI with the specific CALEA (Communications Assistance for Law Enforcement Act). Subject to CALEA requirements are mobile carriers, facilities-based broadband Internet access providers, and VoIP providers – all commonly known as “telecommunications carriers” in the U.S.
Reasons To Choose Our Solution
LI helps law enforcement to quickly identify and analyze data from various sources that are thought to be connected to unlawful activities. LI simplifies the lawful access of law enforcement entities to requested data. No more complications with special equipment that is expensive in deployment and maintenance.
LI supports VoIP, records calls’ whereabouts, as well as supports voice recording of non-ETSI deployment. The solution we offer works in all available networks, including landline phone networks and the Internet.
Features
Totally legal
For each specific legislation and procedure, we scrutinize requirements, what-ifs, what-nots, etc. So your personal solution will be tailored to fit your specific situation the best.
Support
Our specialists are always ready to help and prompt you in complicated situations. Our professional experience counts 15+ years.
Statistics
Easy-to-use tools onboard: links analysis, real-time alerts, dashboards, etc.
Data extraction
LI is capable of retrieving the necessary metadata from intercepted traffic.
Benefits
DPI Technology Use
Deep Packet Inspection technology allows to intercept traffic and perform behavioral analysis. Collected data can be visualized and prepared for further analysis. With the use of DPI technology, the operator receives not only standard functions of the deep traffic analysis system but also its additional options: CG-NAT, BNG, protection against DDoS, etc.
Reliable Hardware Platform
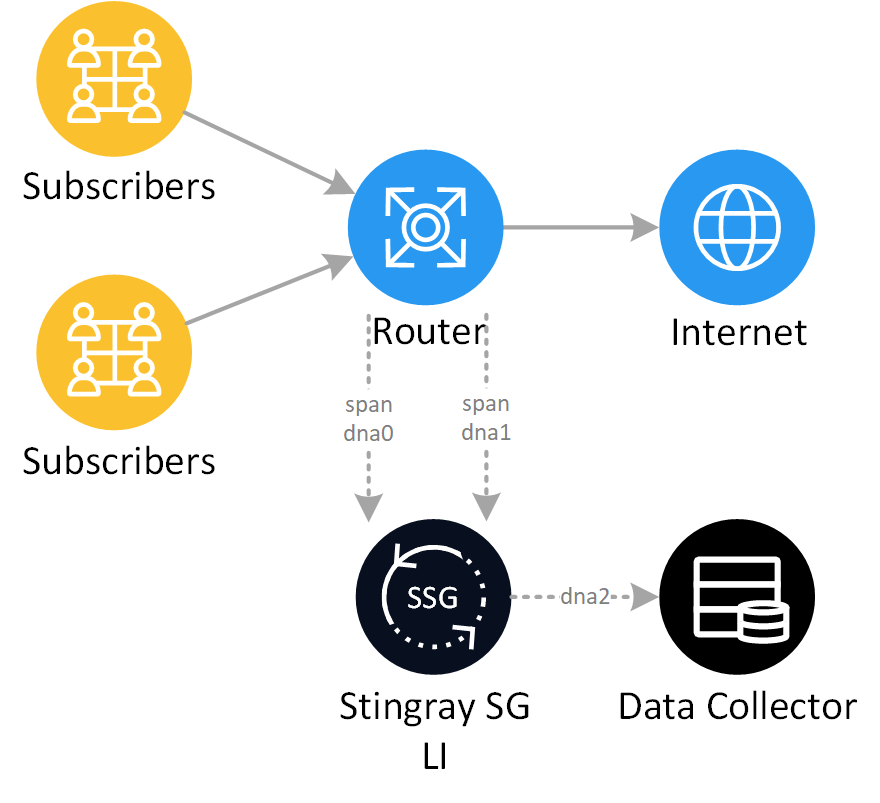
The Stingray SG Lawful Interception equipment does not make any changes to the carrier’s network. To filter traffic we use reliable high-performance x86-servers, and the data is stored in systems with scaling and backup support. To work with the system, a special control panel is used.
Comprehensive Access to the System
Access to the LI equipment and collected information is carried out at any time and is provided to authorized officers, who have the necessary access rights to the control panel. Secure communication channels are used.
Associated documentation

