
How it works
With the CG-NAT solution, ISP has the ability to allocate a public IPv4 address to multiple clients. Thus it is easier to implement IPv6 by extending the use of IPv4. The Stingray Service Getaway traffic monitoring and analysis system is designed for ISPs, but you can also use it to replace NAT devices in your IT infrastructure. The solution is designed to work effectively in any environment: in case if your network infrastructure grows or changes it is easy to adjust it to your needs.
Alternatives
Here are some of CG-NAT alternative solutions and their advantages and disadvantages from their users’ point of view.
- A10 Networks Thunder. As advantages users notice democratic pricing with no sudden changes, high reliability of the solution, as well as rare failures, ease of use, intuitive graphical interface, and detailed documentation. Among the disadvantages, users name the solution’s problems with tracking simultaneous use of multiple ports.
- F5 BIG-IP. Users like the ease of use, a good system of protection against external intrusion, and a large number of available and flexible functions. On the other hand, there are the weak sides of the solution like sagging speed, occasional connection problems, and the fact that it gives little information in case of problems (so sometimes it is not very clear how exactly the situation can be fixed).
- Cisco ASR 9000. Users like the familiar Cisco ecosystem, reliability, and ease of use. As for disadvantages, they notice problems with documentation and occasional bugs in the internal architecture.

Also, you can implement CG-NAT independently with the help of your technical specialists. There are examples of successful cases on telecom-related resources. As an advantage in this case – the possibility of full control of the solution from your side (your engineers would understand the exact architecture of the solution). The main disadvantage is that creating CG-NAT functionality on your own is constant hard work and requires resources . So it is more likely for many companies just to use an out-of-the-box solution.
Pros of CG-NAT as part of Stingray SG
- It makes the use of IPv4 address space the most efficient way.
- It meets requirements specified in RFC 4787 (Network Address Translation (NAT) Behavioral Requirements for Unicast UDP) and RFC 6888 (Common Requirements for Carrier-Grade NATs), which is a guarantee of stable operation of the system.
- Stingray Service Getaway can perform 128 million sessions at a time.
- You can dynamically scale the solution and increase throughput without traffic interruption.
- Unified management of all platform functionality.
- Translations are logged and available either as logs or can be transferred to an external collector via NetFlow v10 (IPFIX).
How to set up NAT in Stingray SG
It can be easily set up in just two commands.
Create a profile with a single command, here it is:
fdpi_ctrl load profile --service 11 --profile.name test_nat
--profile.json '{ "nat_ip_pool" : "5.200.43.0/24,5.200.44/25",
"nat_tcp_max_sessions" : 2000, "nat_udp_max_sessions" : 2000 }'
The other command to turn it on:
fdpi_ctrl load --service 11 --profile.name test_nat --ip 192.168.0.1
or:
fdpi_ctrl load --service 11 --profile.name test_nat --login test_subs
or:
fdpi_ctrl load --service 11 --profile.name test_nat --cidr 192.168.1.0/24
CG-NAT management via a graphical interface
- Load on profiles and NAT address pool
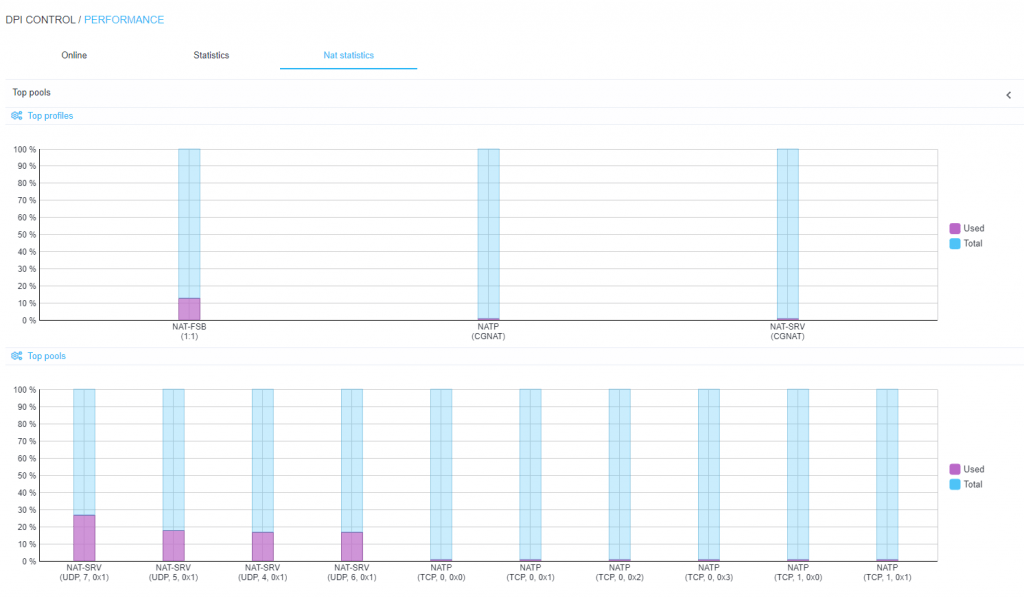
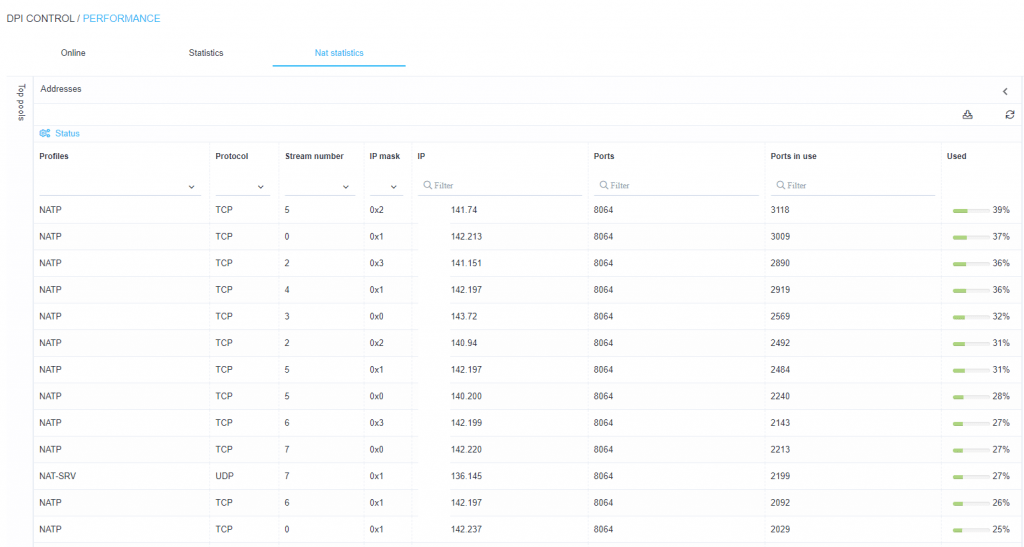
- NAT statistics (port load)
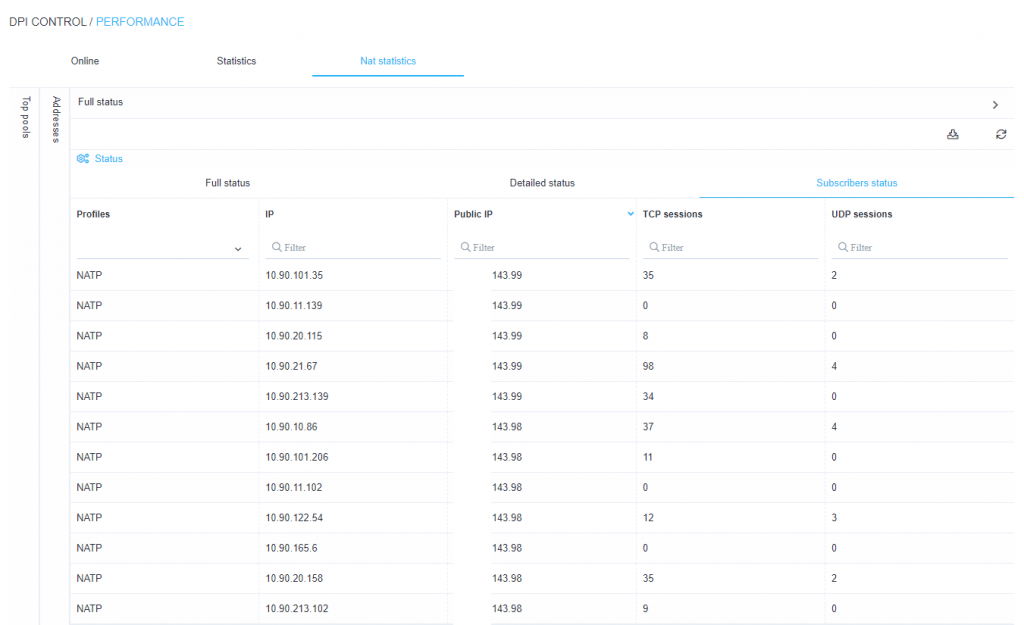
- Statistics on the conversion of private IP addresses to public ones
Features
Stingray Service Getaway has a built-in Full Cone NAT option that allows packets to be sent from any source on an external mapped TCP/UDP port. This makes it easier to monitor the activity of peer-to-peer services (such as torrents, games, etc). All client connections from one internal IP address are bound to one external IP address because of Paired IP address pooling.
There is also basic protection against DDoS attacks . It works simply like this: if an attempt is made to connect to an external address from the outside on a certain port, then the NAT device checks if there are any connections set up for that port. If there is none, the connection will be terminated.
Besides that, in the situation, if one of the subscribers gets infected by malware , we can limit the number of used UDP and TCP ports, so it will not take all network resources. In this case, not all of the subscribers will be infected but only one of them.
Also, there is a technology named Hairpinning . It allows all subscribers behind a NAT to access each other’s public addresses without forwarding packets outside the device and translating outside the device.
Note
The Stingray SG must operate in an in-line mode in order for the CG-NAT function to work correctly.
A Stingray SG BRAS or Complete license is also required for this. Address translation speed depends on the selected license and hardware platform: it can be from 6 to 200 Gbit/s . We also recommend installing a backup platform in case of emergency situations.
