How It Works
Before trying to understand how HTTP works, it’s important to understand the basic features of HTTP. It is connectionless, stateless, and media-dependent. These characteristics are what make HTTP simple, yet powerful.
The process begins with a simple request, let’s say to google.com (Host), asking for a web page. Upon receiving the request, the HTTP server will respond, and the results will be interpreted by an HTTP client.
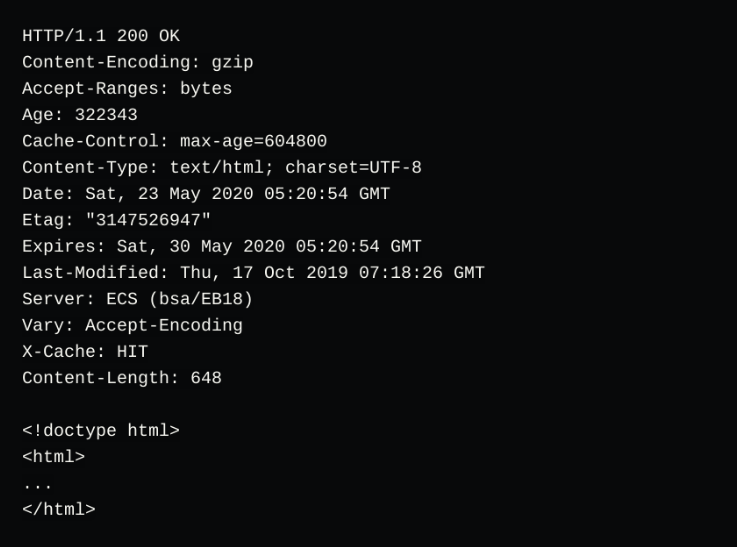
From the response two types of values can be seen, colon-separated values and line-break separated raw data.
Colon-separated key values are headers, and the raw data is a request/response body (Usually containing raw data such as HTML, JSON, etc). The HTTP lifecycle would therefore look like this:
- The browser connects to the google.com server and sends a HTTP request.
- The google.com server receives the request, interprets it, and responds
- The browser receives an HTTP response, interprets it, and renders it depending on the format.
HTTPS
Hypertext Transfer Protocol Secure (HTTPS), is a protocol similar to HTTP but has been built for more security.
Unlike HTTP which does not provide encryption of the information that flows from the server to the browser, HTTPS uses a Transport Layer Security (TSL), formerly known as (SSL) certificate, to add a layer of security to the transmission.
How it works
HTTPS works the same way HTTP does but offers another layer to increase security. Unlike HTTP which uses plain text in its communication, HTTP uses an encryption protocol to make sure that communication is safe. Transport Layer Security (TSL), secures communication by leveraging an asymmetric public key infrastructure. The security approach uses two different keys for communication encryption:
- The public key – This key is available to users that want to interact with the server securely. Information encrypted by public keys can only be accessed by decrypting the information using a private key.
- The private key – This key is maintained by the website owner and exists in the webserver. Its task is to decrypt information encrypted by the public key.
Users can identify sites with SSL certificates by looking at the URL.
HTTP vs HTTPS
As you might have guessed, one of the major differences between HTTP and HTTPS is the Transport Security Layer (TSL). HTTPS also needs an SSL certificate while HTTP can work without one.
The use of HTTPS is rising rapidly, mainly because it influences important factors of business such as SEO and conversion rates.