
What Tasks does the Threat-Intelligence Solution Solve?
- Identification of subscribers with viral activity
- Identification of botnets at an early stage
- Preventive technical support
- Possibility to target subscribers with modern solutions for the protection of end devices
- Work with the security of IoT devices.
Threat Landscape
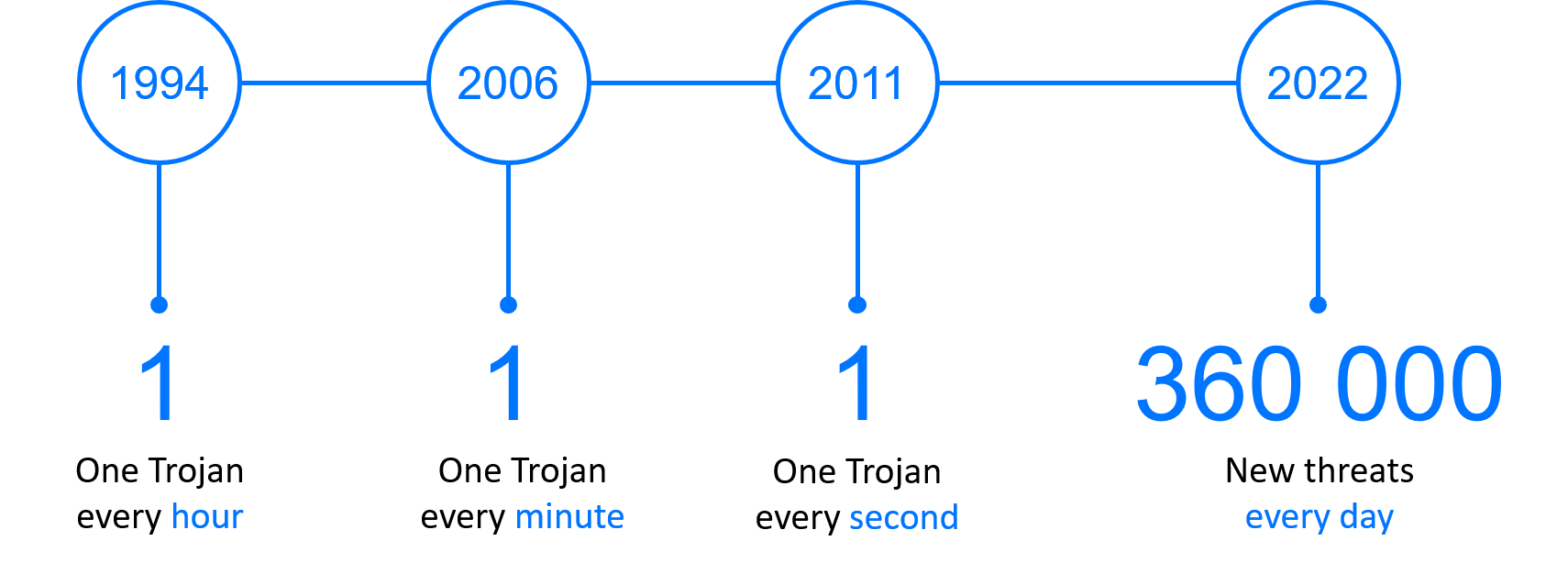
The GReAT — Global Research & Analysis Team — is engaged in the study of cyberthreats at Kaspersky Lab. The leading researcher of security threats Viktor Chebyshev shared the accumulated statistics with us:
- Every day there are 360,000 new security threats on the Internet
- The average damage from a successful cyberattack is $105,000 for medium and small businesses and about $1 million for Enterprise
- All operating systems are sensitive to attacks
- Botnets steal credentials, bank card and crypto wallet data from individuals, and access to critical infrastructure elements and data from companies (for subsequent sale and industrial espionage)
- DDoS attacks in 2022 set records in number and duration
- Vulnerabilities in IoT are actively used for DDoS attacks and the construction of a botnet network — any device from a router to a baby monitor can become a source of infection of neighboring devices in the same network.
Cyberthreat Tracker: The Solution Composition

To implement the threat-intelligence solution, we combined the capabilities of Kaspersky Threat Data Feeds aggregating data on digital threats around the world, and the Stingray SG traffic analytics and policing module.
Kaspersky Threat Data Feeds are a structured, constantly updated and very extensive database of DDoS attacks, phishing sites, the spread of botnets, spam and other types of malicious impact. There are 16 types of feeds, and the Stingray SG works with 7 of them:
- Malicious URL
- Phishing URL
- Botnet C&C
- Mobile Botnet
- IP Reputation
- Ransomware URL
- IoT URL Data
With the help of its own crawlers, spam traps and botnet monitoring systems, Kaspersky Threat Data Feeds as a “virological laboratory” test, analyze and collect data on all known cyberthreats into a single directory.
For Kaspersky + VAS Experts’ joint solution, we place a synchronized copy of the threat database on the server with subscriber behavior statistics.
Based on the comparison, a conclusion is made about potential threats within the operator network:
- Quantitative characteristics appear (how much the network is infected — the number of subscribers and devices),
- as well as a list of identified threats and logins of infected subscribers — for the network administrator to work with specific subscribers.
How to Use?
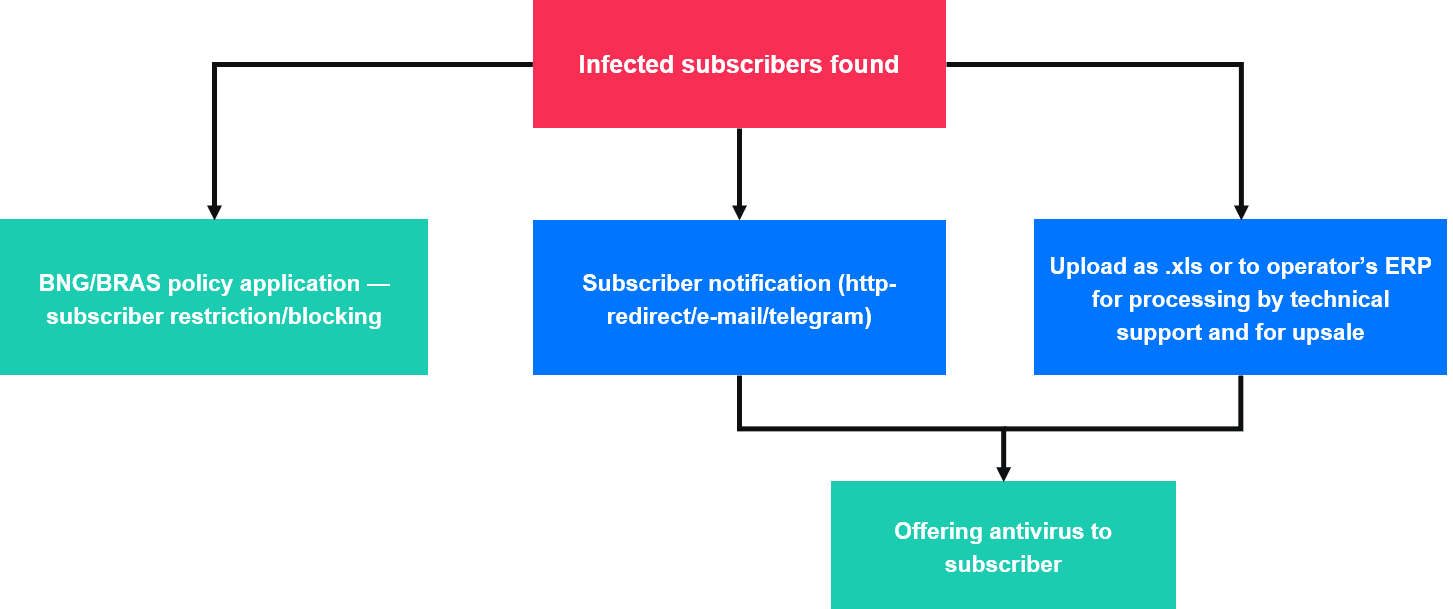
Having determined the degree of infection of the network, the network administrator can solve the problems with the help of the Stingray SG.
Solution Options:
- Restriction or more radical blocking of subscribers using BNG/BRAS policies
- Notification of the subscriber about the suspicious activity of their devices, followed by an offer to purchase an antivirus
- Uploading data about infected subscribers for testing by technical support specialists — also with an option of additional sales.
The second and third options allow additional monetization of Internet provider services.
Further Development
At the moment, the threat tracker is being piloted on the network of several providers. We are improving the accuracy of identifying threats and working out options for the provider’s response to them. A user-friendly graphical interface of the solution is also in development.
We pay special attention to botnets and IoT. The feeds contain the addresses of bot farms. They are used to single out the subscriber whose devices have become part of the botnet. The solution of Kaspersky and VAS Experts will allow, at a minimum, determination of their presence in a particular household, and at most — identification of an infected physical device, even if it is a coffee machine.
We expect that our threat-intelligence solution will help Internet service providers simultaneously solve two tasks: ensuring network security and additional monetization of their services.
For details about the implementation, please contact our specialists as specified on our website.
