
Use case description
- Client with Q-in-Q access type
- FastDPI – traffic handling and policing
- FastPCRF – proxying requests between fastDPI and Radius
- Radius server – receives requests from fastPCRF and generates responses with specified attributes
- Router – responsible for transmitting packets to the Internet and back routing
- DHCP server – responsible for IP addresses allocation from the specified pool.
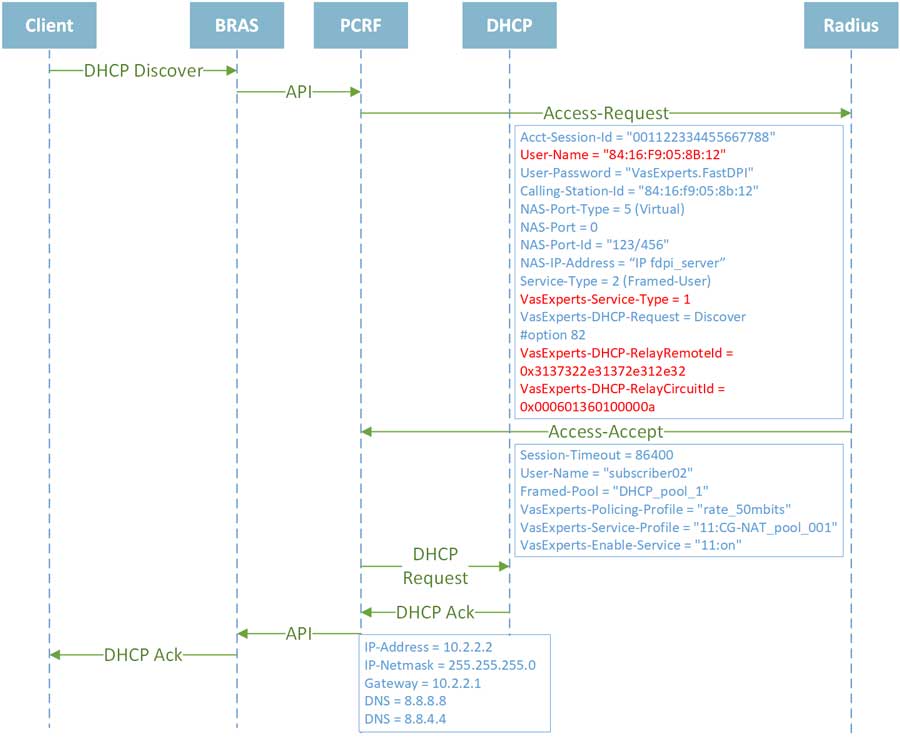
SSG operation algorithm
Starting from SSG version 8.4, support for IP address pools for PPPoE and DHCP Radius Proxy modes is available.
Previously, in these modes, SSG expected to receive the subscriber’s network parameters in Access-Accept from the Radius server. Now it is possible to issue the name of the address pool from which the DHCP server should allocate addresses to subscribers.
It is possible to pass the pool name to the DHCP server using several options, such as 125, 77 and 60 for IPv4, and 15, 17 for IPv6.
In our case, we will use option 125 for IPv4 and 17 for IPv6, since these options are always added in the request. So, the probability that critical data will be overwritten is zero.
To use other options, you need to configure the DHCP server and SSG accordingly.
fastPCRF configuration
To configure SSG, in addition to the basic L2 BRAS configuration, you have to specify the addresses of the DHCP servers and the option the pool name should be passed through.
Deploying and configuring a dhcpd4 server using namespace
To begin with, we are going to deploy another DHCP server on the same server where the SSG is already installed, and it is going to be available only for the SSG platform. This is due to the existence of various corporate policies that regulate the use of DHCP-servers for servicing the operator’s internal network and subscribers.
To do this, we will limit the interfaces that our DHCP server will “listen” to and limit the servers that the DHCP server will respond to. DHCP servers will be run in namespaces other than the common network namespace. We are going to run the DHCP servers in the namespaces which are different from the common network namespace.
First, let’s create a namespace:
# ip netns add DHCP
Create veth:
# ip link add veth0 type veth peer name veth1
Put the interface into the namespace:
# ip link set veth1 netns DHCP
Enable the interfaces and assign addresses to them:
# ip netns exec DHCP ip link set lo up # ip netns exec DHCP ip link set veth1 up # ip link set veth0 up # ip netns exec DHCP ip addr add 192.168.10.2/30 dev veth1 # ip addr add 192.168.10.1/30 dev veth0
Edit the DHCP server configuration file:
#Declaring the opt125 structure for VASExperts
option space VASEX code width 1 length width 1;
option VASEX.poolname code 1 = string;
option space vivso code width 4 length width 1;
option vivso.VASEX code 43823 = encapsulate VASEX;
option vivso.iana code 0 = string;
option op125 code 125 = encapsulate vivso;
#DNS server addresses
option domain-name-servers 192.168.1.4, 8.8.8.8;
#Setting the leasing time
default-lease-time 600;
max-lease-time 7200;
log-facility local7;
#Declare classes
class "vas-pool" {
match if option VASEX.poolname = "test-pool";
}
shared-network MyNetwork {
#Declare a subnet for relay, forbid issuing addresses from it to unknown clients
subnet 192.168.10.0 netmask 255.255.255.252 {
deny unknown-clients;
}
#Declare subnet for vas-pool class
subnet 192.168.3.0 netmask 255.255.255.0 {
pool {
range 192.168.3.10 192.168.3.100;
allow members of "vas-pool";
}
}
}
Run ISC DHCP in DHCP namespace:
# ip netns exec DHCP dhcpd -cf /etc/dhcp/dhcpd.conf
Deploying and configuring kea dhcp6 servers
We will use KEA server as IPv6 DHCP server.
Let’s make the configuration file look like this:
{
"Dhcp6": {
"interfaces-config": {
"interfaces": ["veth3/2a03:dec0:666:2::2"]
},
"control-socket": {
"socket-type": "unix",
"socket-name": "/tmp/kea-dhcp6-ctrl.sock"
},
"lease-database": {
"type": "memfile",
"persist": true,
"lfc-interval": 3600
},
"expired-leases-processing": {
"reclaim-timer-wait-time": 10,
"flush-reclaimed-timer-wait-time": 25,
"hold-reclaimed-time": 3600,
"max-reclaim-leases": 100,
"max-reclaim-time": 250,
"unwarned-reclaim-cycles": 5
},
"renew-timer": 120,
"rebind-timer": 240,
"preferred-lifetime": 180,
"valid-lifetime": 300,
"option-data": [
{
"name": "dns-servers",
"data": "2001:4860:4860::8888, 2001:db8:2::100"
}
],
"shared-networks":[{
"name": "MyNetworks",
"relay": {
"ip-address": "2a03:dec0:666:2::1"
},
"subnet6": [{
"client-class": "test-ipv6-pool",
"subnet": "2403:d4c0:aa::/48",
"reservation-mode" : "disabled",
"pd-pools": [{
"prefix": "2403:d4c0:aa::",
"prefix-len": 48,
"delegated-len": 63
}],
"option-data": [{
"name": "dns-servers",
"data": "2001:db8:2::dead:beef, 2001:db8:2::cafe:babe"
}]
}]
}],
"client-classes": [{
"name": "test-ipv6-pool",
"test": "vendor[43823].option[1].hex == 'test-ipv6-pool'"
}]
},
"Logging":{
"loggers": [{
"name": "kea-dhcp6",
"output_options": [
{
"output": "/var/log/kea-dhcp6.log",
"flush": true
}
],
"severity": "DEBUG",
"debuglevel": 99
}]
}
}
It should be noted that the KEA DHCP server for IPv6 does not work correctly on link local addresses, so we will use global IPv6 addresses.
Let’s create another namespace and name it DHCP6:
# ip netns add DHCP6
Create veth:
# ip link add veth2 type veth peer name veth3
Put the interface inside the namespace:
# ip link set veth3 netns DHCP6
Enable the interfaces and assign addresses to them:
# ip netns exec DHCP6 ip link set lo up # ip netns exec DHCP6 ip link set veth3 up # ip link set veth0 up # ip netns exec DHCP6 ip addr add 2a03:dec0:666:2::2/64 dev veth3 # ip addr add 2a03:dec0:666:2::1/64 dev veth2
There is the Framed-Pool attribute in Access-Accept when the client is connected:
VasExperts-User-Name = "testuser" Framed-Pool = "test-pool" Framed-IPv6-Pool = "test-ipv6-pool" VasExperts-Enable-Service = "9:on" VasExperts-Multi-IP-User = 1 VasExperts-Service-Profile = "11:user_nat"
After the connection is established, we check if the addresses are issued correctly:
Rec#0
MAC=18:0F:76:01:05:19 login='testuser'
SessionId=0x01bc (net=0xbc01) phase=[3] network
Times (now=764039602395618 ticks)
created: 2020/01/27 14:33:55, -427.849052s (762838183927452 ticks)
last packet: 2020/01/27 14:41:02, -0.805806s (764037339656521 ticks)
phase start: 2020/01/27 14:33:57, -425.829550s (762843854773358 ticks)
session_timeout=0, idle_timeout=300, stop_reason=0
idx_slave=1, idx_iface=0, pppoe_max_mru=1492, acct_started=0, ip4_rejected=0, ip6_rejected=0
LCP:
LCP state [9] opened
counters: restart=10, failure=5, peer-failure=5, terminate=2
ts_retrans: 2020/01/27 14:33:55, -427.785471s (762838362464891 ticks)
MRU=1480 Auth-proto: [3] MS_CHAPv2
request_id=0x34, service_req_id=0x01, my_magic_number=0x5f10c4ae, ping_counter=5
IPCP:
IP=192.168.3.13 GW=192.168.1.254 DNS1=192.168.1.4 DNS2=8.8.8.8
Framed-Pool: [test-pool] DHCP-Server=192.168.10.2 lease-time=599
next renew: 2020/01/27 14:41:56, +53.178381s (764188929568748 ticks)
IPCP state [9] opened
counters: restart=10, failure=5, peer-failure=0, terminate=2
ts_retrans: 2020/01/27 14:33:57, -425.829547s (762843854783043 ticks)
request_id=1
Statistics packet/bytes: subs->inet=636/59860, inet->subs=0/0
IP6CP:
local=fe80::809a:d869:d86e:d032
prefix=2403:d4c0:aa:2::/64
PD=2403:d4c0:aa:3::/64
Framed-IPv6-Pool: [test-ipv6-pool] Prefix=2403:d4c0:aa:2::/63 server-DUID=[0x0001000125BDB112C2DD08604508] lease-time=240
next renew: 2020/01/27 14:43:33, +150.472972s (764462136946903 ticks)
IP6CP state [9] opened
counters: restart=10, failure=5, peer-failure=0, terminate=2
ts_retrans: 2020/01/27 14:33:57, -425.826606s (762843863041510 ticks)
peer_iface_id=3661548372820007552, dhcpv6_iid=1, request_id=1
Statistics packet/bytes: subs->inet=71/8712, inet->subs=0/0
----------
TOTAL: 1 recs
To automate the creation of namespace, we will write the script createNetworkNamespace.sh and add it to autorun (remember to grant permissions to run this script):
#!/bin/bash #If you get "Object "netns" is unknown, try "ip help".", then you should install this modules #yum install -y https://repos.fedorapeople.org/repos/openstack/EOL/openstack-icehouse/epel-6/kernel-2.6.32-358.123.2.openstack.el6.x86_64.rpm #yum install -y https://repos.fedorapeople.org/openstack/EOL/openstack-grizzly/epel-6/iproute-2.6.32-130.el6ost.netns.2.x86_64.rpm #Add new namespace ip netns add dhcp #Add new link ip link add veth0 type veth peer name veth1 #Set veth to namespace dhcp ip link set veth1 netns dhcp #Turn on interface ip netns exec dhcp ip link set lo up ip netns exec dhcp ip link set veth1 up ip link set veth0 up #Set IP addresses to interfaces ip netns exec dhcp ip addr add 192.168.10.2/30 dev veth1 ip addr add 192.168.10.1/30 dev veth0 #Run dhcpd in namespace ip netns exec dhcp dhcpd -cf /etc/dhcp/dhcpd.conf #Add new namespace ip netns add dhcp6 #Add new link ip link add veth2 type veth peer name veth3 #Set veth to namespace dhcp ip link set veth3 netns dhcp6 #Turn on interface ip link set veth2 up ip netns exec dhcp6 ip link set lo up ip netns exec dhcp6 ip link set veth3 up #Set IP addresses to interfaces ip addr add 2a03:dec0:666:2::1/64 dev veth2 ip netns exec dhcp6 ip addr add 2a03:dec0:666:2::2/64 dev veth3 #Run kea in namespace ip netns exec dhcp6 /usr/local/sbin/keactrl start -s dhcp6
We will add it to autorun via rc.local. To do this, add a line like this to this file:
sh /your/path/to/createNetworkNamespace.sh
Now, when the server is rebooted, the necessary namespaces will be created and DHCP servers will be started in these namespaces.
DPI-based BNG is a solution that allows not only subscriber policing, but also Quality of Experience metrics and traffic balancing for each subscriber and device. Contact us to learn more about the SSG platform and its use on service provider networks.