
What is DLP?
DLP (Data Leak Prevention) – is the practice of preventing leaks of confidential information from the information system. DLP works as a set of technologies and methods that help organizations prevent the loss or unauthorized disclosure of sensitive data. The main goal of DLP is to identify, monitor, and protect private information.
To protect enterprise information, a simple, fast, and variable solution will be to transfer critical data to the server and deploy the DLP system, preferably in conjunction with the DPI, which we will describe later. This approach extends standard access controls, such as logins and passwords, directory and file access policies.
How does DLP work?
The DLP system is usually a modular software product, less often a hardware product. The system is based on the dataflow analysis outside the corporate network and/or its specific segment.
The classic DLP system consists of the following modules:
- analyzer – a network component whose task is to monitor traffic, as well as record statistics from switches and routers of the corporate network, including flow, with subsequent transfer to storage systems
- storage system – collects, stores and processes the received data
- graphical module – is responsible for visualization of data and reports, as well as output of monitoring results to the information security officer
- external module – in some DLP systems, the external module is designed for direct installation on the user’s PC for subsequent tracking of keystrokes on the keyboard, a picture on the monitor screen, the contents of RAM, as well as controlling the movement/copy/delete of files on disk devices.
DLP Solution Types
The infographic system above can be considered perfect if it is supplemented by Deep Packet Inspection (DPI), a deep traffic analysis technology.
DPI technology allows to:
- conduct network security audits and identify external attacks, as well as take countermeasures to eliminate them with notification of personnel
- analyze the status of all network connections and decide whether to terminate them
- gather statistics on protocols, applications, services, as well as on the direction of traffic and even on a particular user with subsequent logging
- generate traffic for the target server to test its performance and resistance to attacks.
Data Loss Prevention Policies
Properly configured DLP policies can significantly reduce the risk of leakage of confidential information and improve overall security for your organization.
DLP policies are based on conformance requirements and industry security standards. There is a risk that the requirements will become outdated over time, so they need to be revised and updated in accordance with the new rules and threats.
Data Loss Prevention tools and technologies
DLP continuously monitors data flows to detect any unauthorized use of sensitive data. This is possible thanks to the built-in monitoring of network traffic, which allows to track various types of data communication: emails, file transfer, etc.
When the DLP system detects unauthorized activity on the network, it automatically sends a warning to the security team or blocks the data transfer, which helps prevent information from being leaked or stolen. To provide additional protection to sensitive data, DLP systems can encrypt or mask data so that unauthorized users cannot read it.
DLP systems generate audit reports and logs to ensure visibility of data activity and compliance with current policies. This helps organizations monitor and analyze data usage and identify any potential security risks.

Why would companies use DLP systems?
Data loss can be a serious problem for any company. Implementing a DLP system will be useful for any organization that is concerned about the security of corporate information.
Critical information can be lost due to unforeseen circumstances, such as technical failures, cyber-attacks or human error.
The DLP system helps prevent unauthorized access to critical data, which helps avoid financial losses, legal responsibility, and damage to corporate image in future.
This is how may look the network layout of a modern company that cares about the security of corporate information:
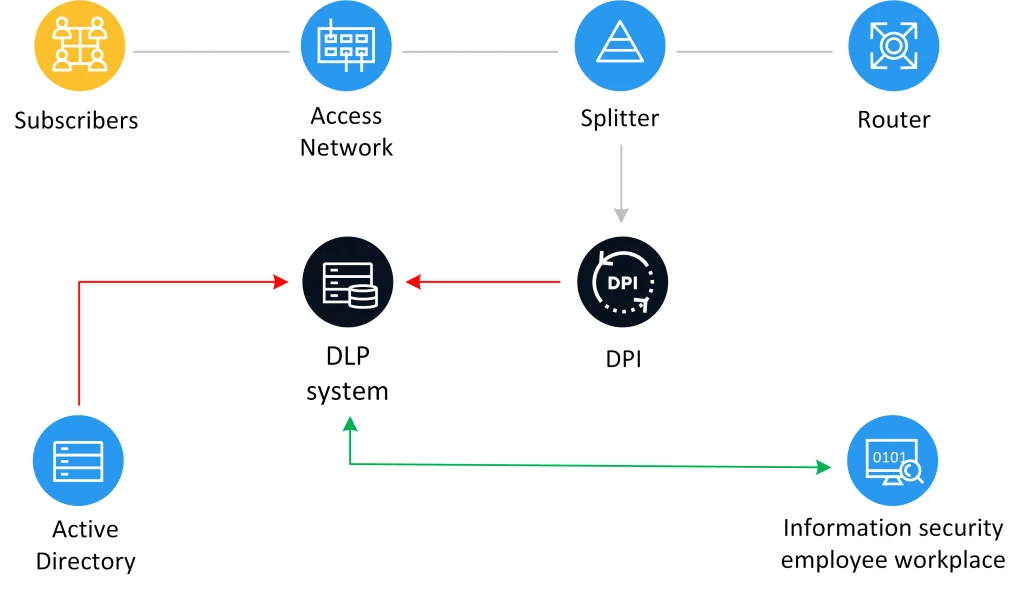
DLP System Use Cases
Companies should choose the type of DLP solution that best meets their security and regulatory requirements.
- The DLP system controls sensitive traffic data such as documents, numbers of credit cards or social security cards. It can prevent data from leaking by blocking or encrypting it.
- DLP Endpoint Detection and Response (EDR) solutions track data transfers to PCs and mobile devices. They can block or encrypt data transmission if DLP policies are violated.
- DLP systems allow to track email messages and attachments for sensitive data. They can prevent users from sending e-mails containing private information or encrypt data.
- Cloud DLP systems control data stored in cloud applications. They can prevent unauthorized users from sharing or accessing data.
- DLP systems for databases monitor database activity to detect and prevent leaks. They can also help organizations meet regulatory requirements such as PCI DSS, HIPAA, or GDPR.
- DLP with Insider Risk Management solutions monitor user activity to prevent potential security risks caused by employees or contractors. They can track users’ access to specific files or print documents.
Recommendations for Data Loss Protection
Regular audits are required to ensure compliance with DLP policies and identify potential security risks. Auditing can include viewing user activity logs, scanning vulnerabilities, or penetration testing.
Employee training is important to preventing data loss. Employees should be trained on how to handle sensitive data, how to identify potential security risks, and how to report suspicious activity.
It is necessary to ensure that they comply with DLP policies and do not pose security risks.
Conclusion
The development of digital technologies and social engineering raise questions about the security of confidential information. Today’s DLP systems that use DPI technology will make it possible to analyze data flows beyond your corporate network at high speeds (up to 400 Gb/s) and prevent sensitive information from leaking beyond your corporate network.
Confidential data leakage prevention systems from Russian manufacturers, such as the DLP system based on Stingray SG from VAS Experts, are ready to upgrade networks for any speed. The ability to scale performance is due to the use of standard x86 servers, and the speed of traffic processing can reach 3.84 TB/s. In case of any questions and problems, 24-hour technical support will quickly and efficiently resolve any issue.