
Brute Force is an attack method that is used to crack passwords by calculating every possible combination. The shorter and simpler the password, the less time and resources are required to select it. This method is often used to create botnets of infected devices.
In case Brute force activity with the subsequent BotNet is detected in the network, the telecom operator is threatened with IP address blocking.
Detection of a brute force attack
Stingray platform generates Full NetFlow in IPFIX format, which is sent to a special Quality of Experience module. The user experience data has the following metrics:
- Round-trip-time (RTT)
- Indicators of the number of retries
- The number of sessions, devices, agents
- IP addresses per subscriber
- Traffic distribution by application and transport protocols
- Traffic distribution by autonomous system (AS) numbers
- Clickstream for each subscriber.
Short and frequent sessions give us a clue about an attempt to crack the device. Examples of protocols that can be hacked: SSH, HTTP, HTTPS.
By enabling the ssh-bruteforce trigger in the QoE module, the network engineer will receive notifications about cracking attempts and quickly react. One can choose the type of notification: by e-mail (to one or more addresses with a customized template) or HTTP (the resource is called by the GET or POST method).
Triggers and notifications
Triggers process statistics on traffic and analyze the data in the background mode. In the case of Brute force, the report displays a TOP list of hosts that were accessed via the ssh protocol.
The report is generated on the basis of three key metrics:
- session life time
- number of sessions per subscriber per period
- application layer protocol.
When the number of sessions per one subscriber is large (more than 100 per 1 subscriber by default), and the lifetime of these sessions is short, then you can suspect that someone is trying to guess a password: in other words, an attacker does a large number of authorization attempts in short time.
It is a system trigger and is available in both QoE module licenses: Lite and Standard.
Case study
This example shows 105 sessions per 1 subscriber.
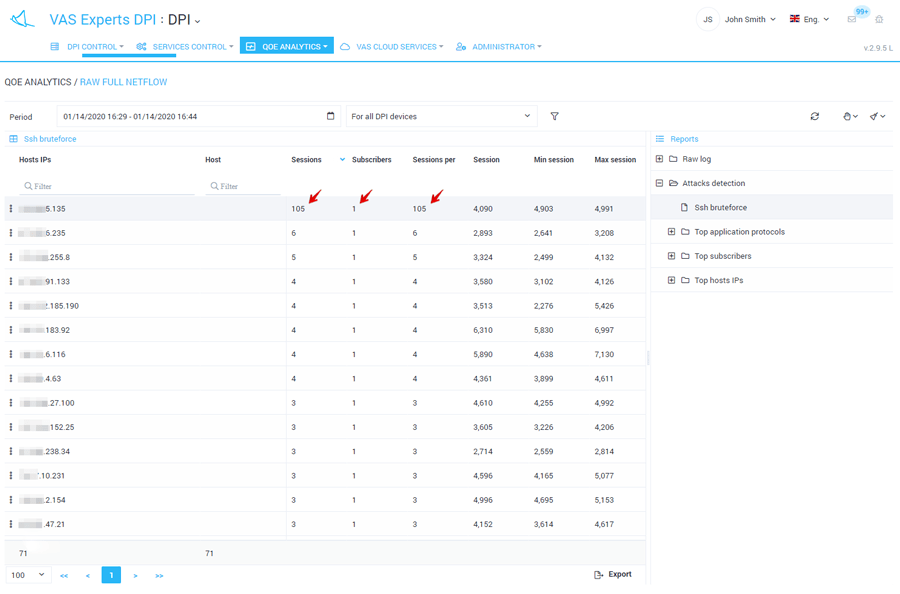
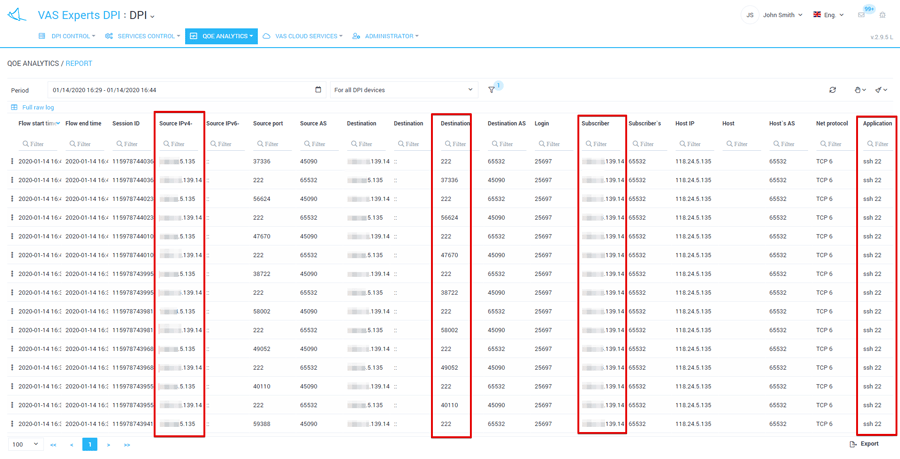
Based on the QoE report, the system allows you to create more detailed reports to see the specifications in the raw Netflow log. Information is available:
- by session duration
- IP of the subscriber and the host
- ports and autonomous systems numbers.
In this report, we observe a certain host brute-forcing a subscriber’s password.
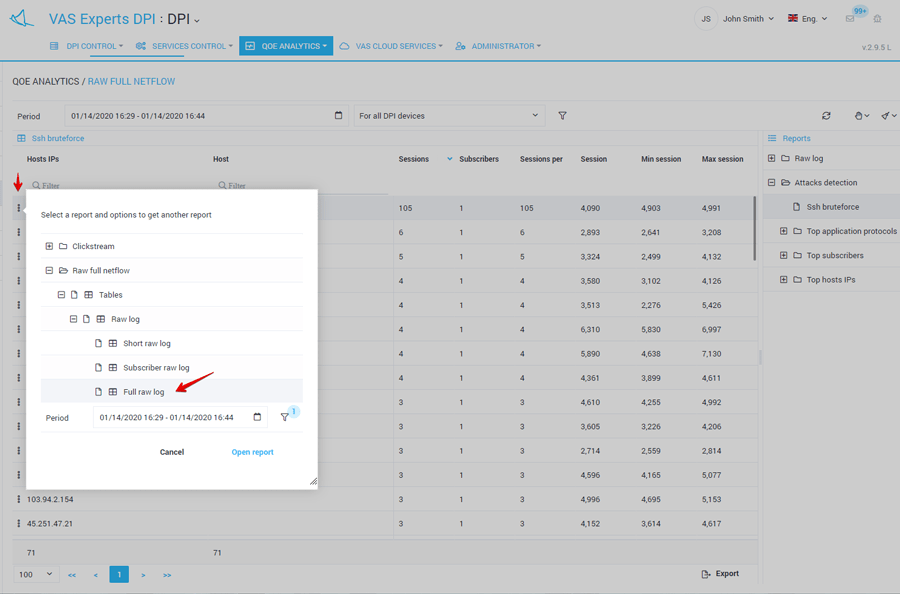
What should you do when a brute force attack is detected?
The first thing an Internet provider can do is to contact the subscriber, notify him and offer to make the password more complex. Subscriber can also be warned by displaying a banner or by posting information on the start page via the “Service Management Advertising” section.
Secondly – to enable the mini-Firewall option for a certain subscriber. This Stingray Service Gateway function is necessary to ensure the safe use of the Internet, protect the network from overloads and malicious software. The mini-Firewall is built into the platform solves two main tasks:
- prevent hacking via open ports that may be attacked;
- block harmful activity outgoing from the subscriber.
What passwords are cracked most often?
Default login and password are provided in most encrypted systems where a user can authorize. Ideally, each user should change the default password to his own after first entering the system, however, many neglect this simple security rule or set too simple combinations for easier remembering. Thus, entire groups of vulnerable passwords are formed:
- Simple sequences (keyboard-walks): qwerty, qazwsx, 123456
- Phrases and words that often come to mind when creating a password: password, admin, root, access
- Passwords that partially duplicate logins, for example, with the addition of numbers: user123.
Statistics:
- according to https://haveibeenpwned.com/, more than 9 billion accounts have been discredited to date;
- more than 555 million entries are exposed in the “password dictionary”;
- the largest number of botnet hosters (botnet C&C – command & controllers) is located in the USA followed by Russia and the Netherlands.
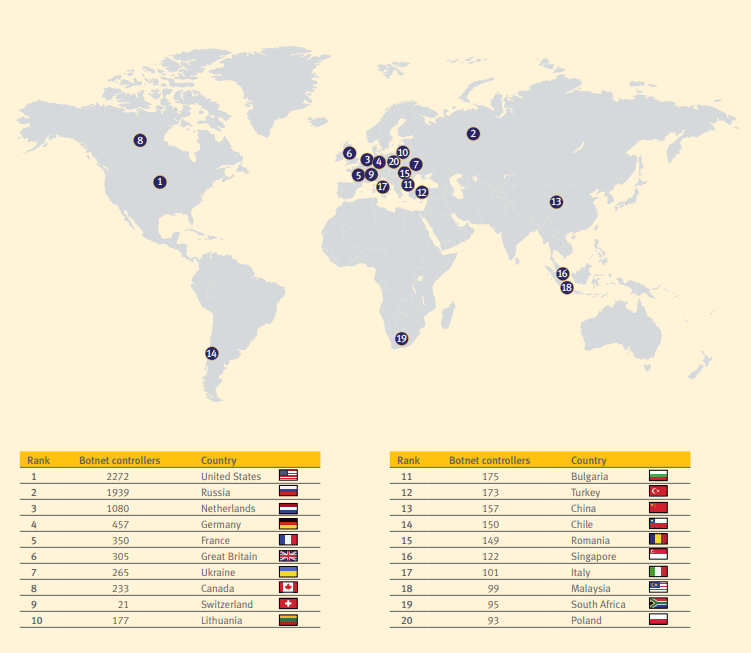
Spamhaus Botnet Threat Report 2019
To summarize
Typically, infected devices are used for DDoS attacks, sending spam, viruses, organizing cryptocurrency mining, downloading user personal data, cyber blackmailing. The object of Brute Force can be ordinary Internet users as well as commercial and state-owned companies. Sometimes discredited passwords and other data are sold to further expanding of the infected network.
Installing the Stingray platform with the mini-Firewall option and the QoE module allows you to secure the network from DoS and DDoS attacks, analyze traffic and control overloads. You can learn more about the benefits and other functionality of the deep traffic analysis system from VAS Experts specialists.